ISCC2022 writeup
Reverse
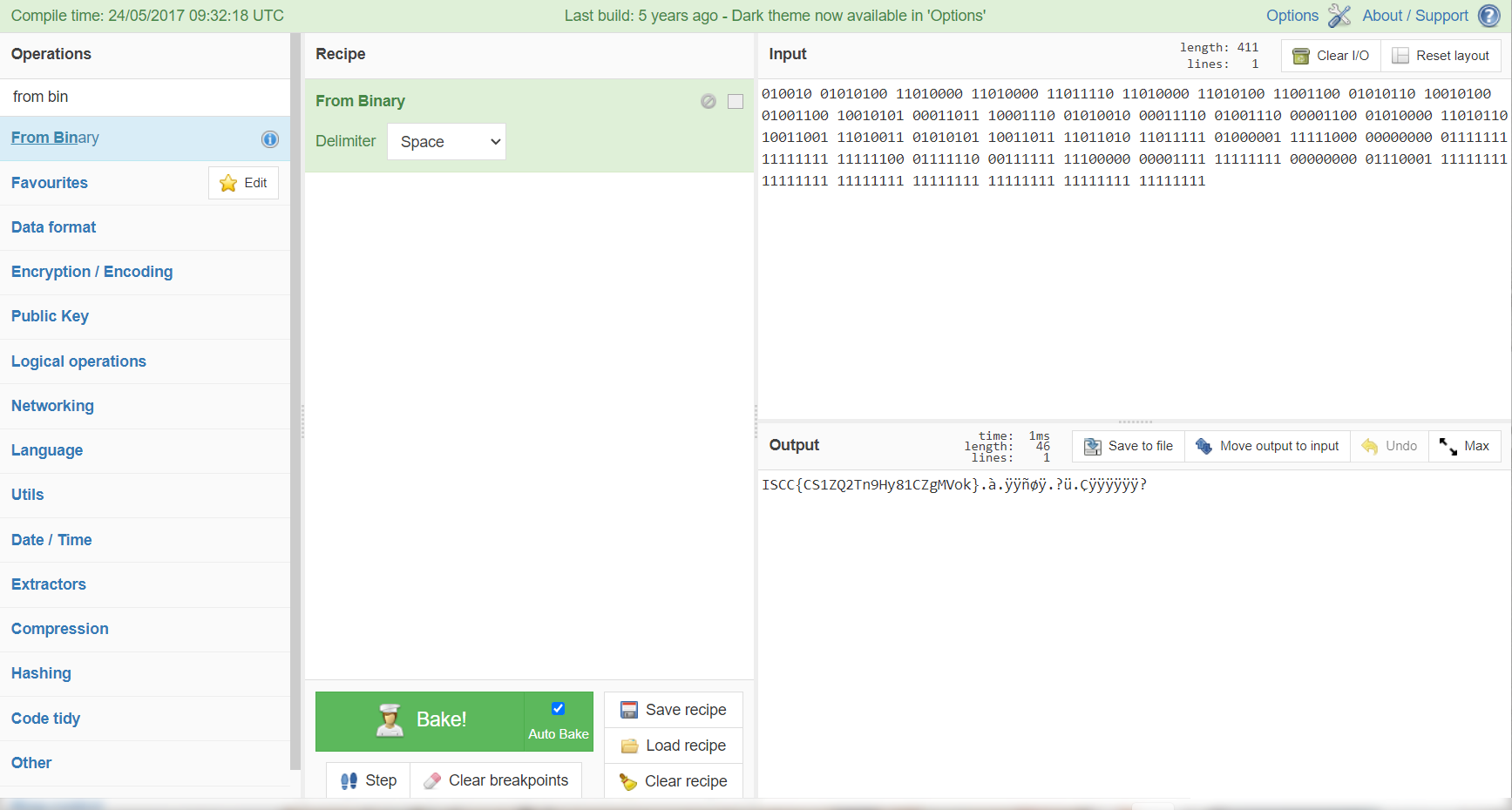
GetTheTable
下载附件,查个壳
64位程序无加壳
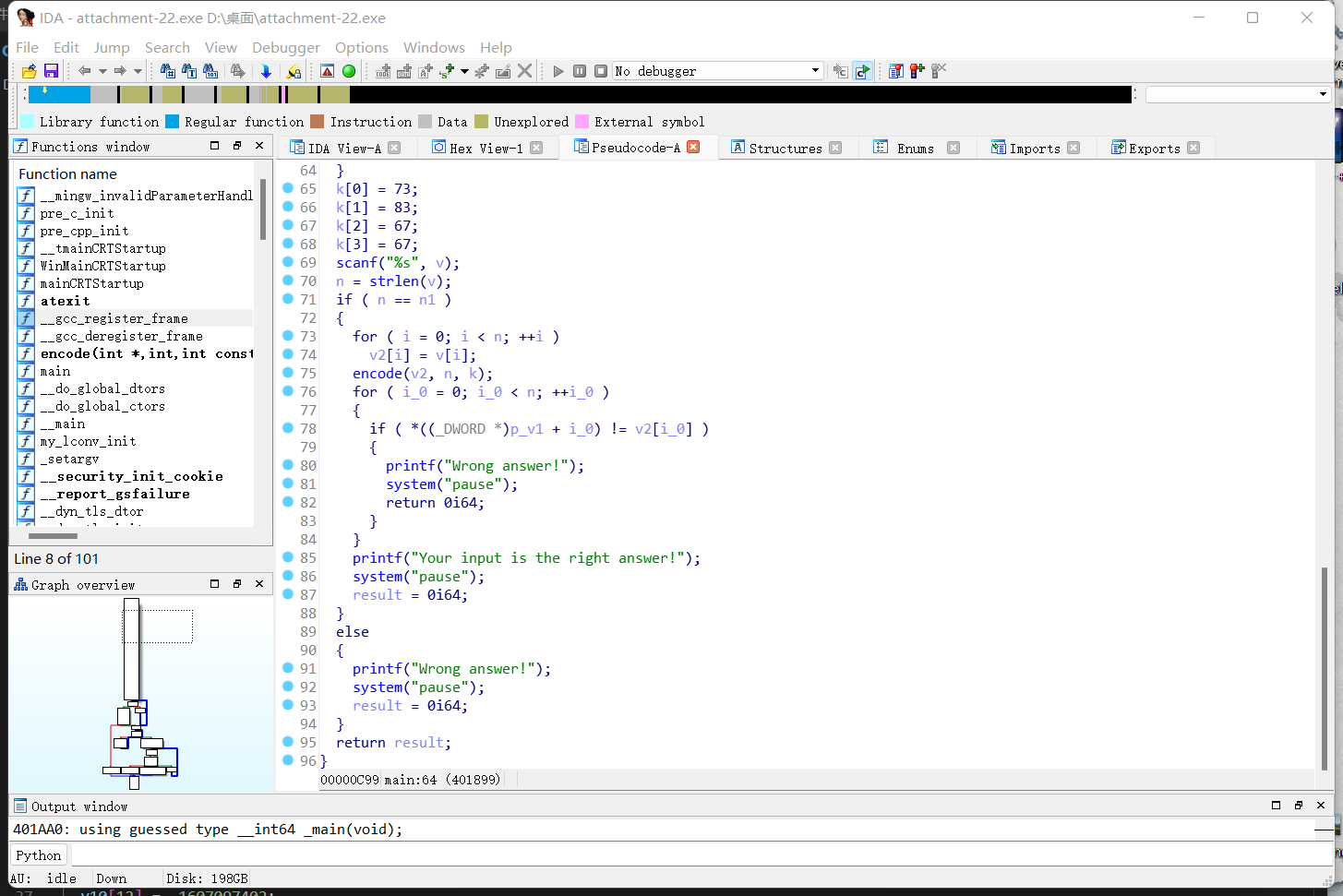
用IDA打开,反编译一下查看主函数伪代码
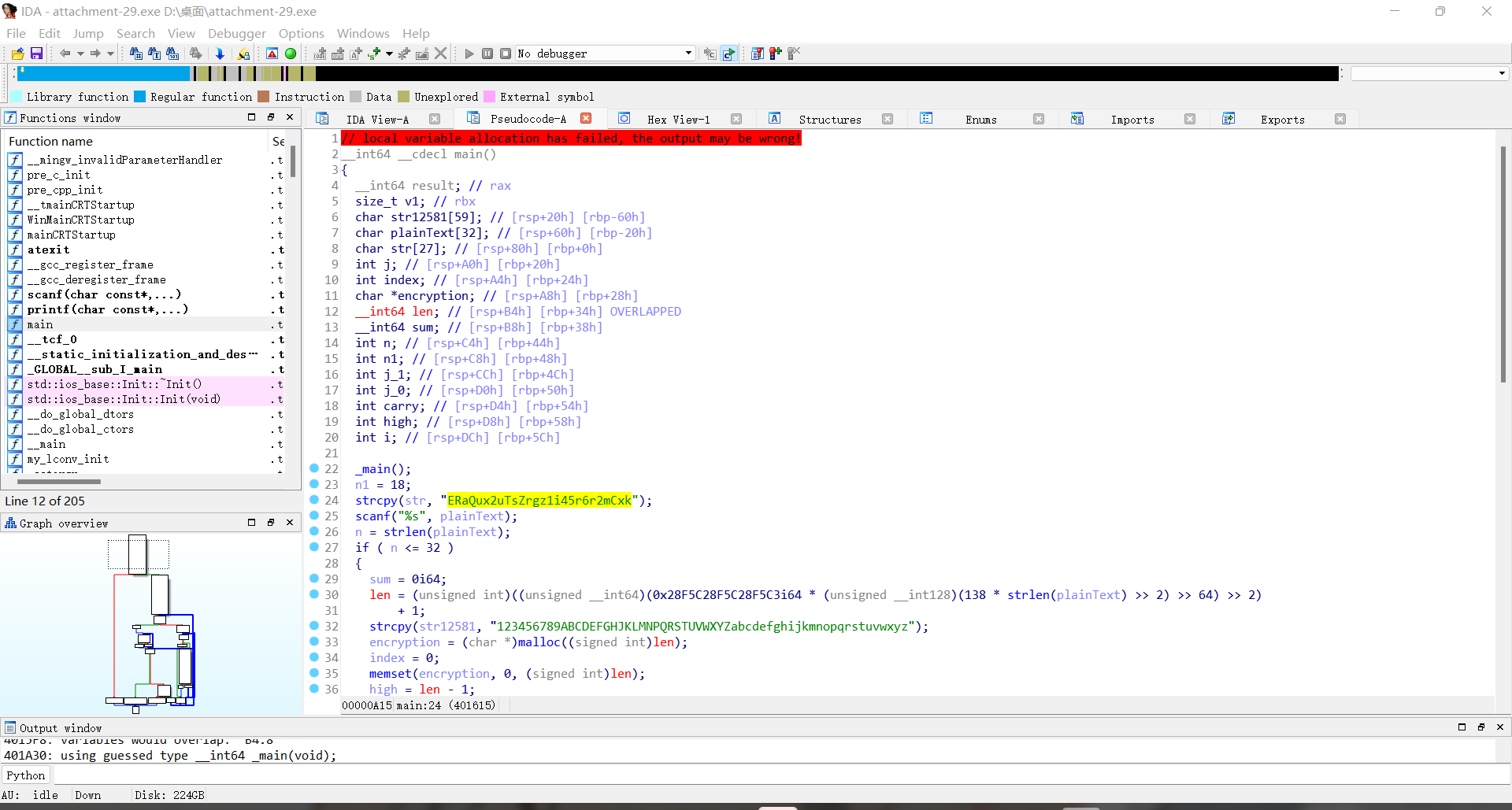
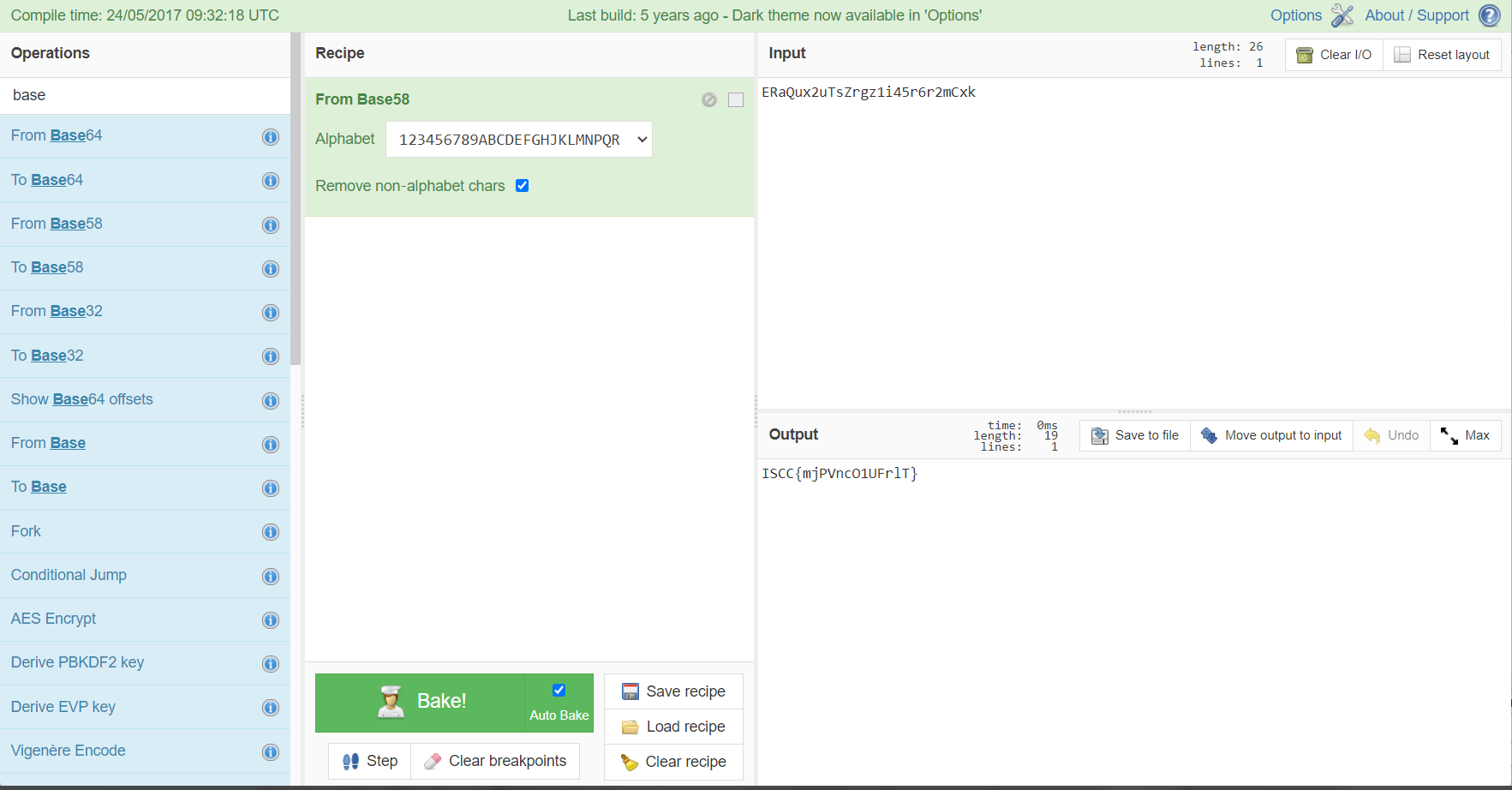
将str字符串拉去base58解码即可得到flag
Amy’s Code
下载附件,打开提示我们输入flag

先用PEID查个壳
可以看到是用C语言写的32位exe文件,没有加壳
将附件丢进IDA反编译
f5查看伪代码
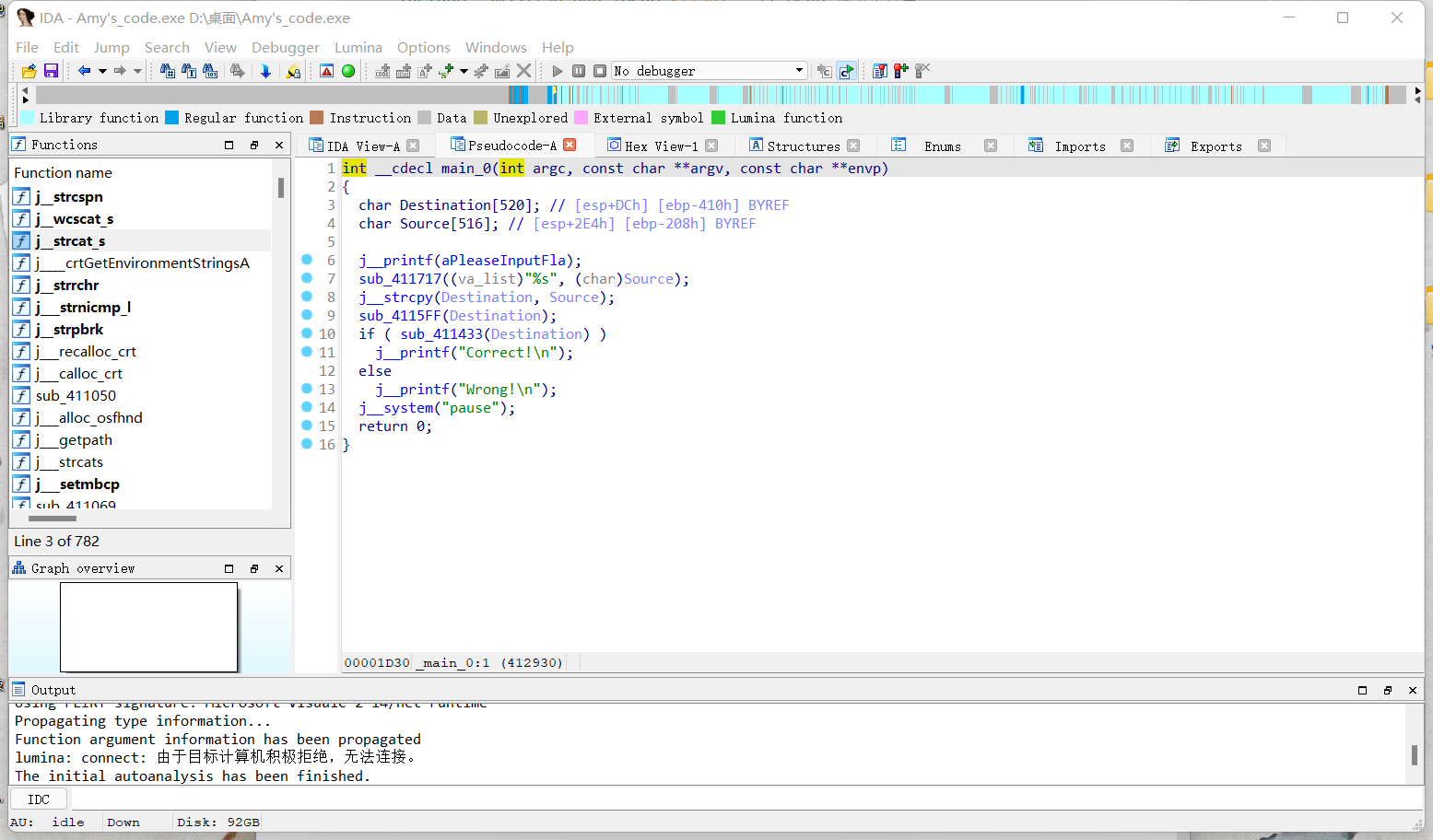
源代码如下:
1 | int __cdecl main_0(int argc, const char **argv, const char **envp) |
简单分析一下源代码
sub_4115FF函数的作用是将flag中每一位字符和其相对应的位数进行异或。
sub_411433函数的作用是定义新列表v6和v9,将v6中的每一位字符和进行异或后的flag中的对应位的字符相加得到新列表v4,再和v9比较,相同则返回1,不同则返回0.
分析完毕,得到逆向思路:
先将v9和v6中的对应位相减,得到异或后的flag
由于异或是可逆的运算,所以将得到的flag再次异或就可以得到正确的flag
代码如下:
1 | #获取异或后的flag |
How_decode
老规矩 先查个壳
丢进IDA找到主函数反编译一下查看伪代码
简单分析一下源代码
发现是魔改过的XXTEA加密
加密过程如下
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
IDA快捷键H可以把十进制数转为16进制!(关键)
解密脚本如下:
1 | from ctypes import * |
Sad Code
下载附件,查壳软件查一下壳
32位的 C++
丢进IDA里面反编译一下查看主函数
加密函数如下:
1 | int __cdecl main_0(int argc, const char **argv, const char **envp) |
简单分析一下源代码
重点是if语句中的代码,是一个八元一次方程组
编写解密脚本如下:
1 | // 解方程组 |
Bob’s Code
查个壳
32位C程序,无加壳
IDA反编译一下,查看主函数
主函数
代码如下
1 | int __cdecl main_0(int argc, const char **argv, const char **envp) |
简单分析一下
分布加密,依次看一下
加密1
加密代码如下
1 | unsigned int __cdecl sub_412560(int a1, unsigned int a2, int a3, unsigned __int8 a4) |
加密2
加密代码如下
1 | unsigned int __cdecl sub_4127C0(int a1, unsigned int a2, int a3, char a4) |
加密3
加密代码如下
1 | int __cdecl sub_412D10(int a1, int a2, char a3, int a4) |
分析一下’
1 | int a1 = v8 |
加密4
加密代码如下
1 | size_t __cdecl sub_412BF0(char *Str, int a2) // a2 = 2 |
解密脚本
我是憨批
1 | import base64 |
输入源代码中的str2
即可得到flag
VigenereLike
下载附件 IDA反编译查看主函数
找到main 函数打开
main 函数代码如下:
1 | __int64 __fastcall main(int a1, char **a2, char **a3) |
定位到v24字符串
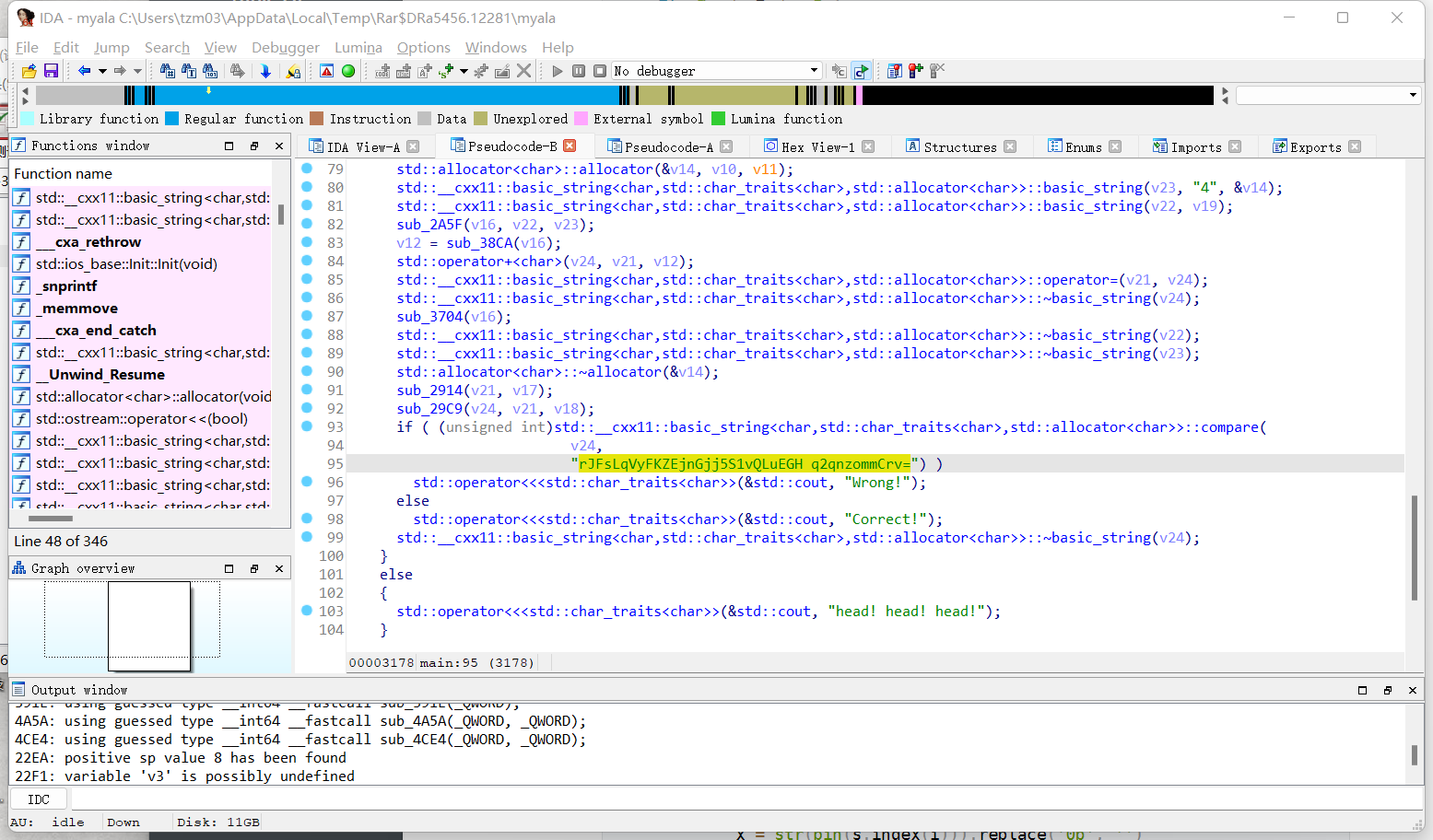
代入解密脚本如下:
1 | # -*- coding: utf-8 -*- |
Ruststr
用IDA打开附件中的文件
F5反编译查看主函数
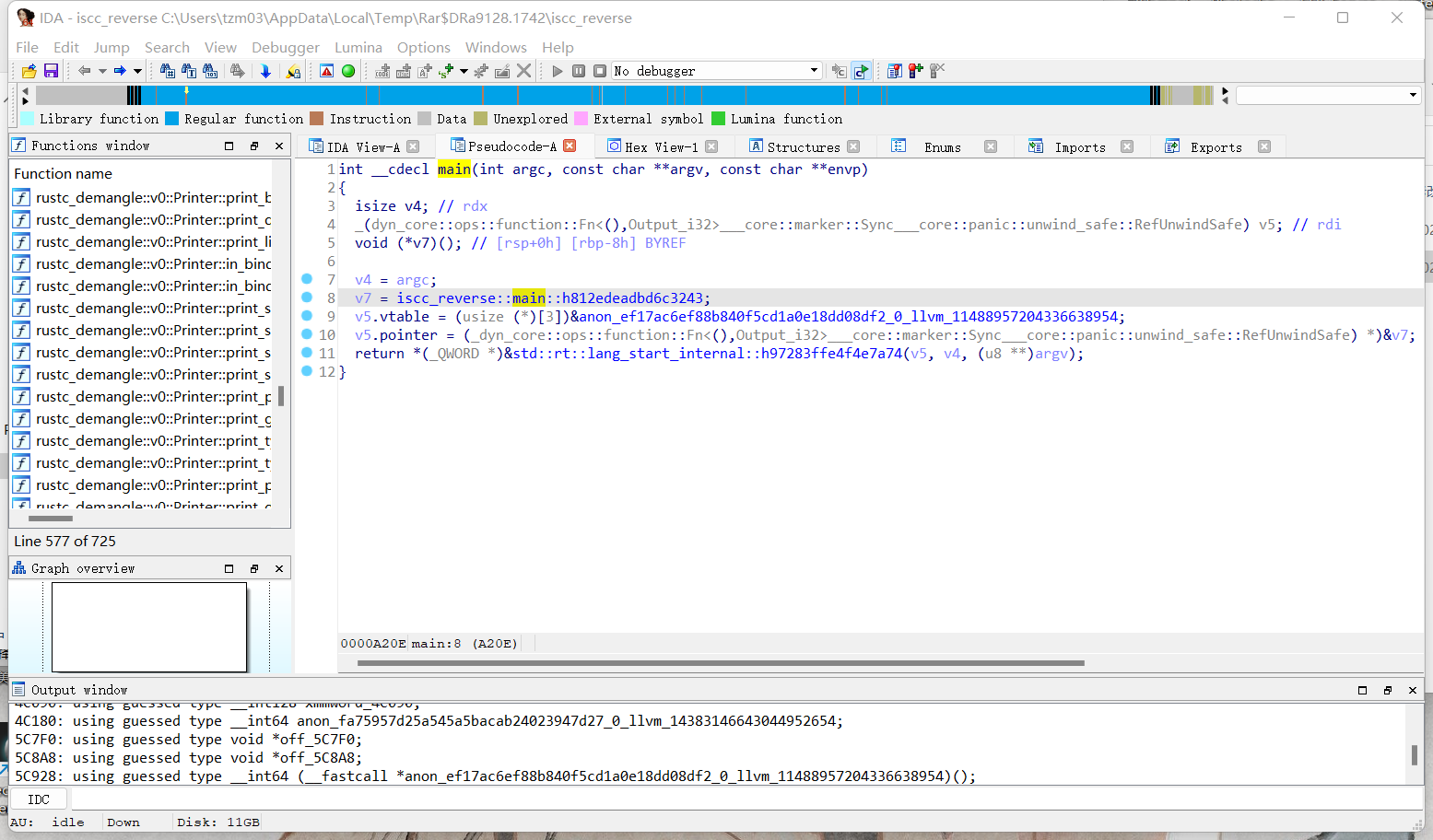
可以找到一串base64的字符串
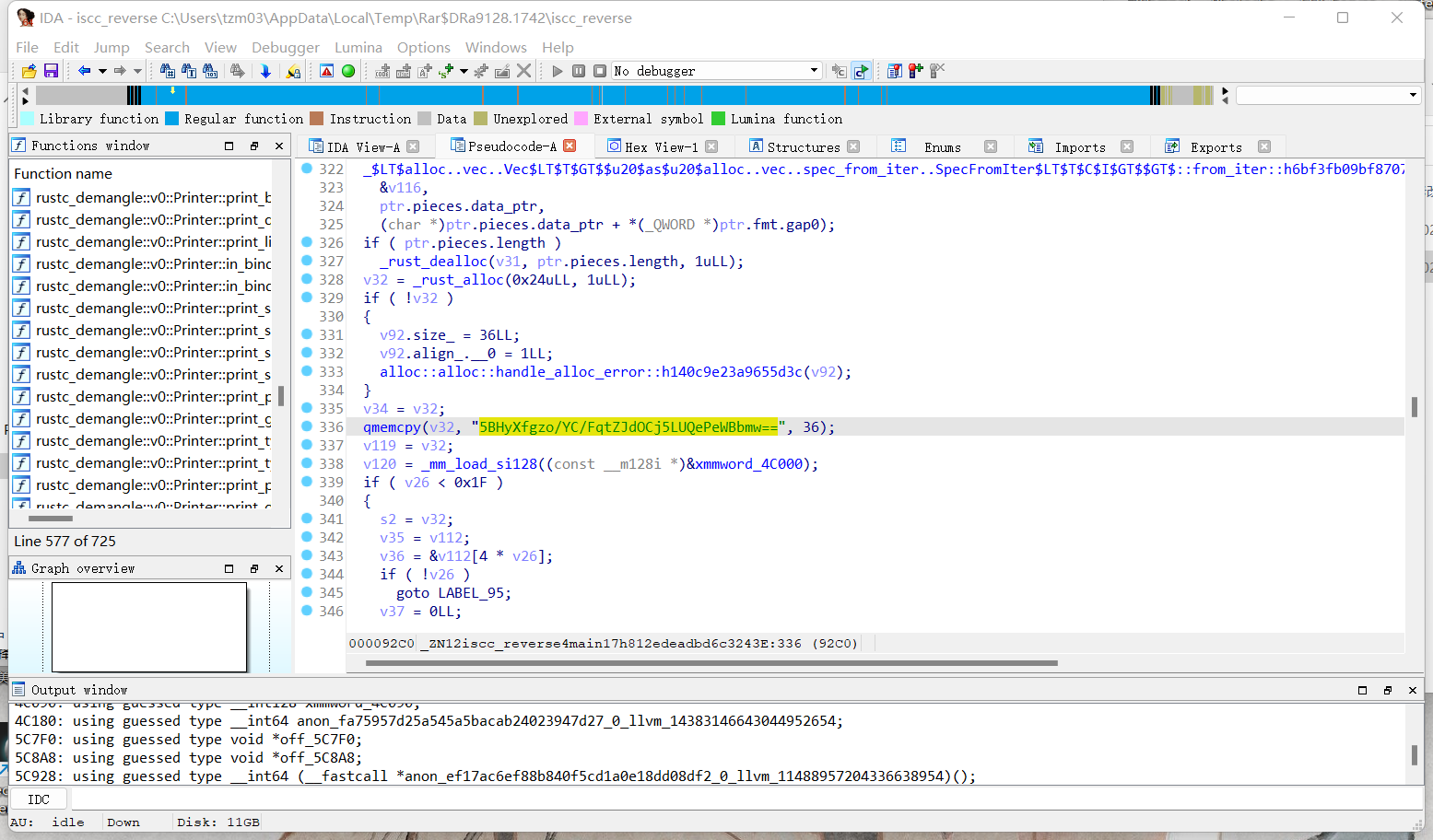
代入解密脚本
1 | import base64 |
Mobile
MobileA
安卓逆向题,用Jeb打开附件,寻找MainActivity
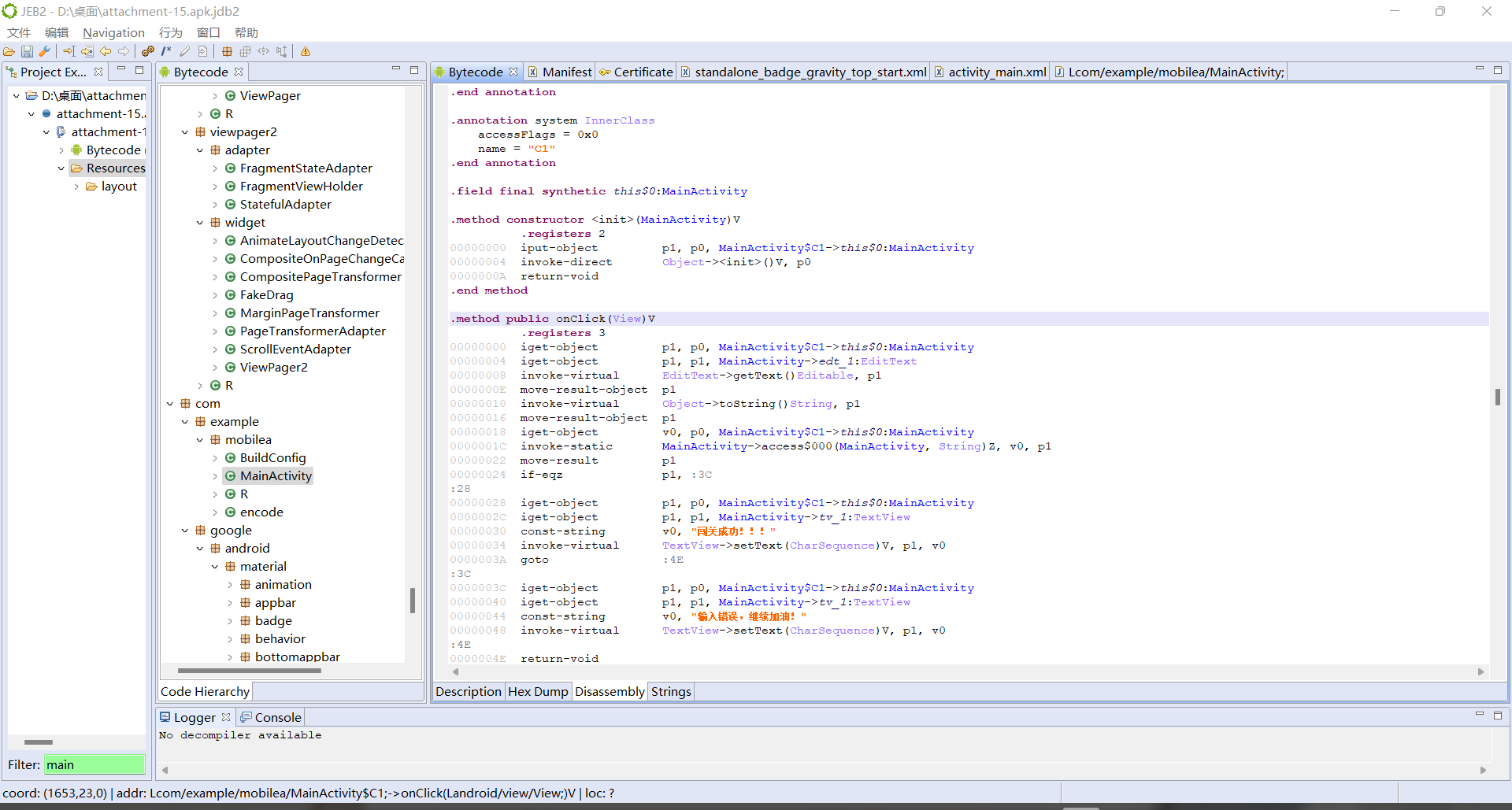
Jeb快捷操作: Q-转换成为代码
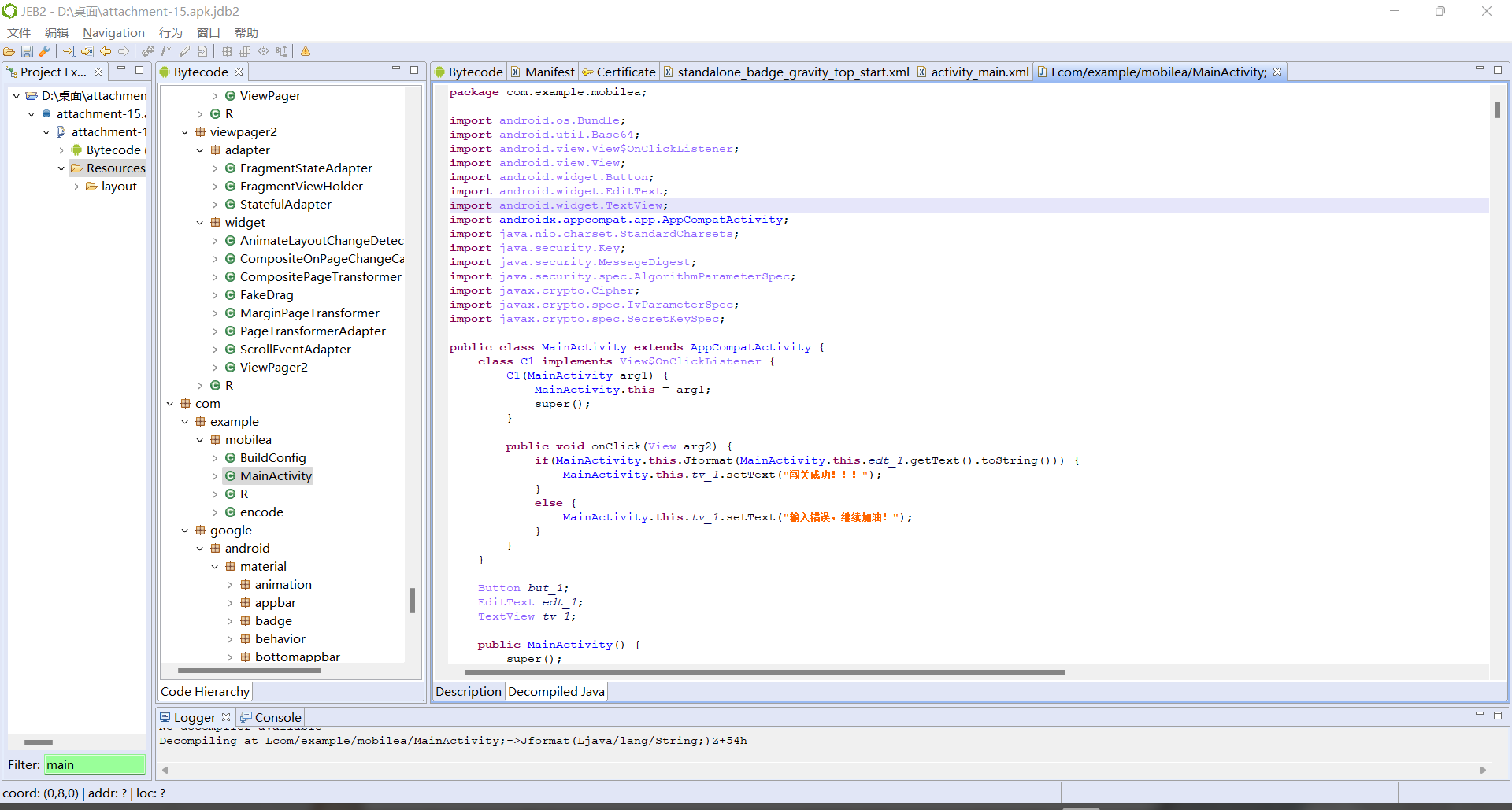
完整代码如下:
1 | package com.example.mobilea; |
MSIC
2022冬奥会
题目提示 本次冬奥会吉祥物的设计原型
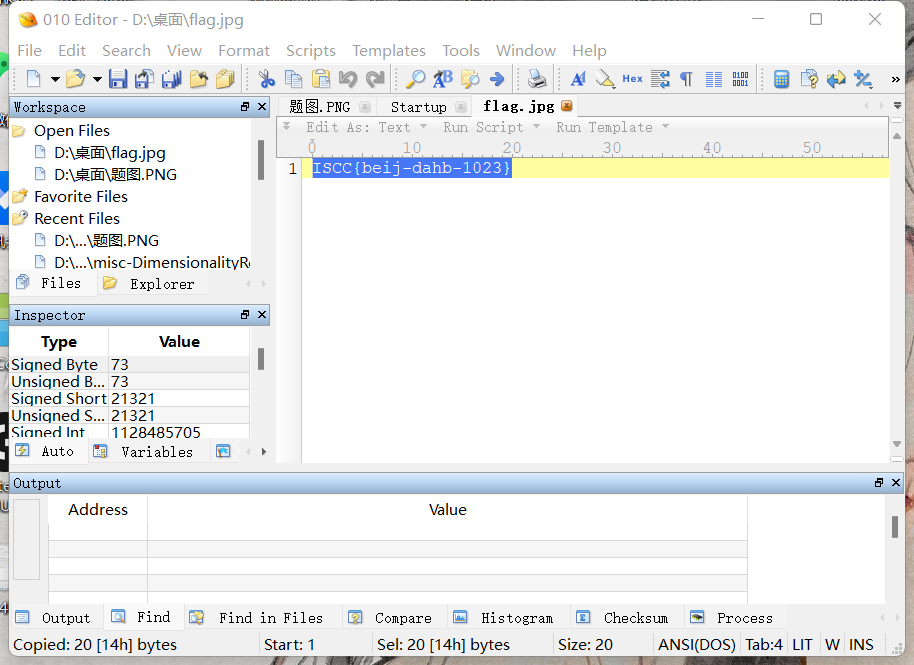
下载附件 发现其中有一个加密的jpg文件
猜测密码为 ‘熊猫’ 或者 ‘灯笼’
‘灯笼’实验成功, 但发现图片打不开,拖到010里面查看即可得到flag
单板小将苏翊鸣
附件是中包含一张图片和一个名为flag.txt的加密文件
可见突破口在图片中
显然这个图片的长宽不匹配
将图片用010editor打开
将图片的长改成与宽一致
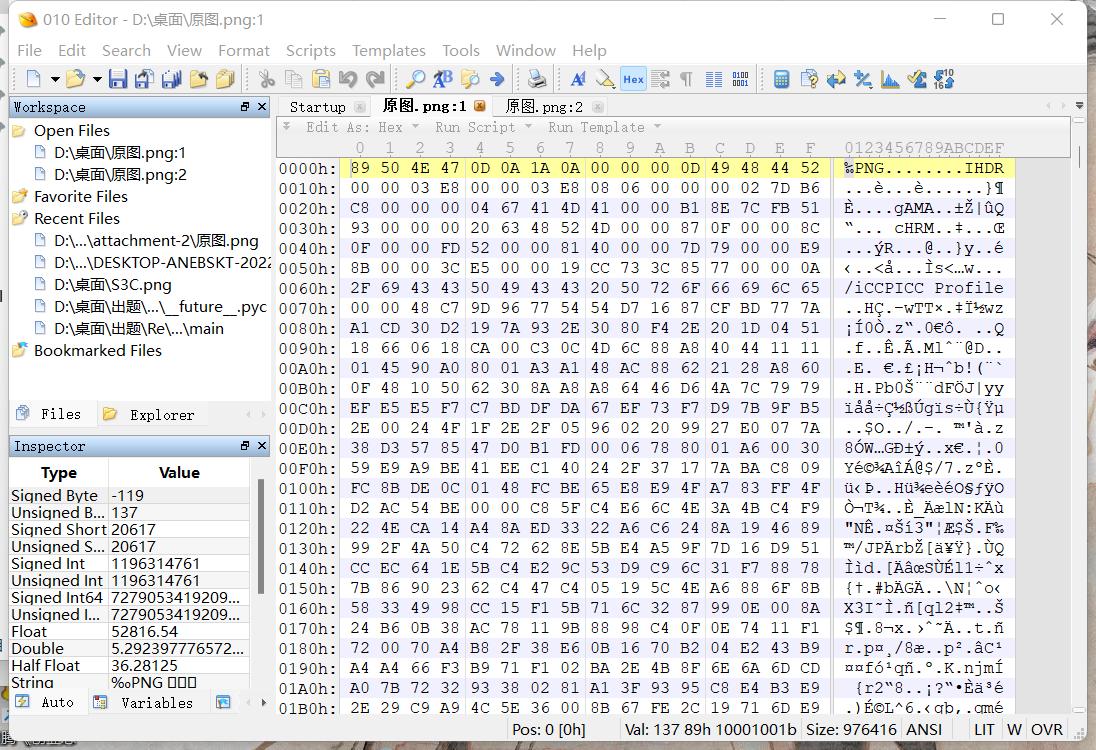
保存后就可以得到一张大小完整的图片

扫码后可以得到一串编码
可以看出是汉字unicode编码
百度搜索在线转换解码
得到提示:密码应该是本次冬奥会中我国的总奖牌数和金银铜牌数
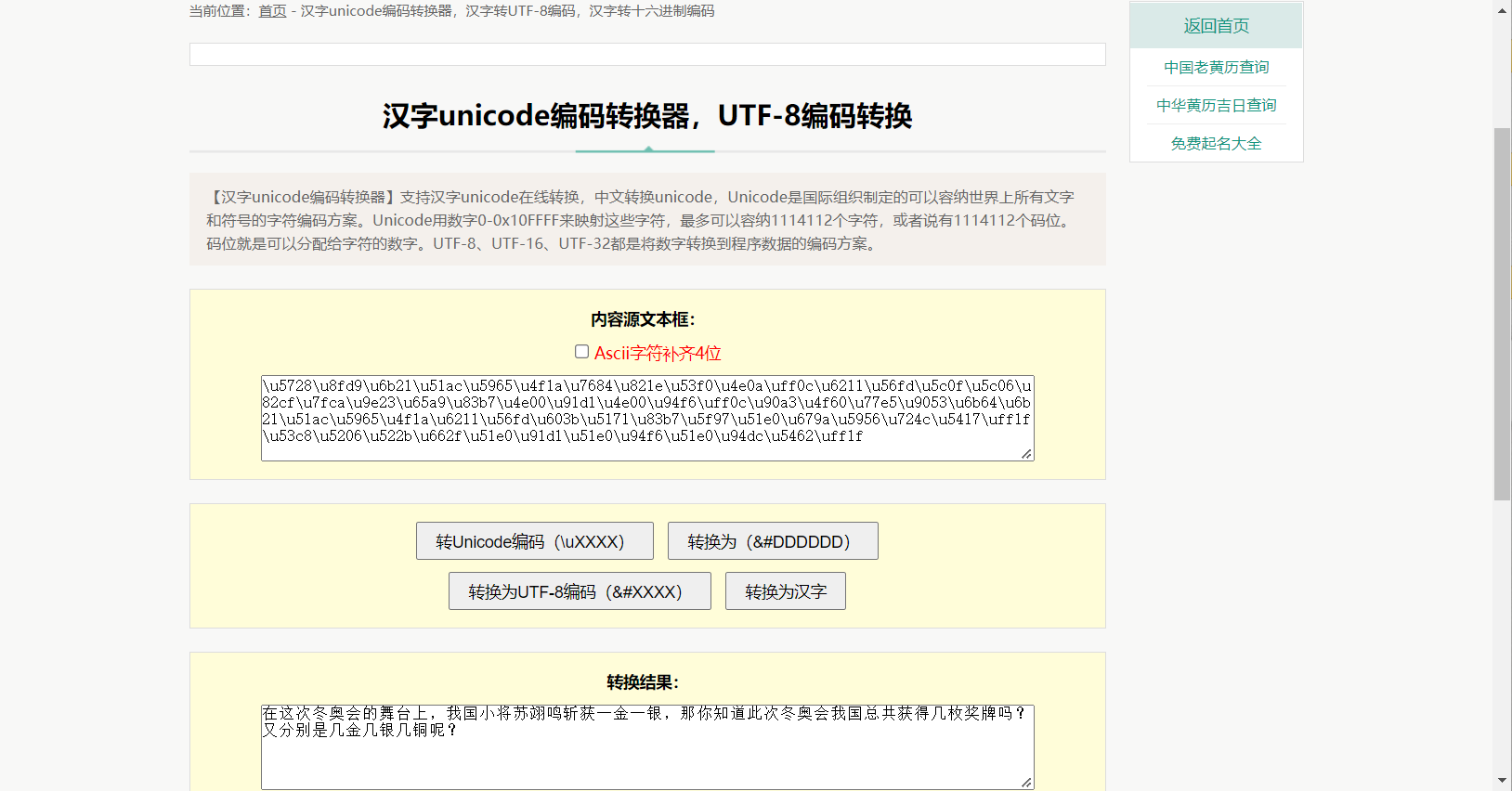
得到密码打开加密的txt文件就可以得到flag
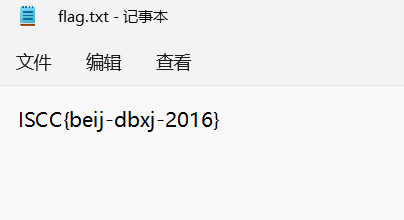
藏在星空中的诗
下载附加,可以看到一共给了三个文件:一个txt,一个加密的excel还有一个.psd文件
用photoshop打开.psd文件可以看到有两个图层
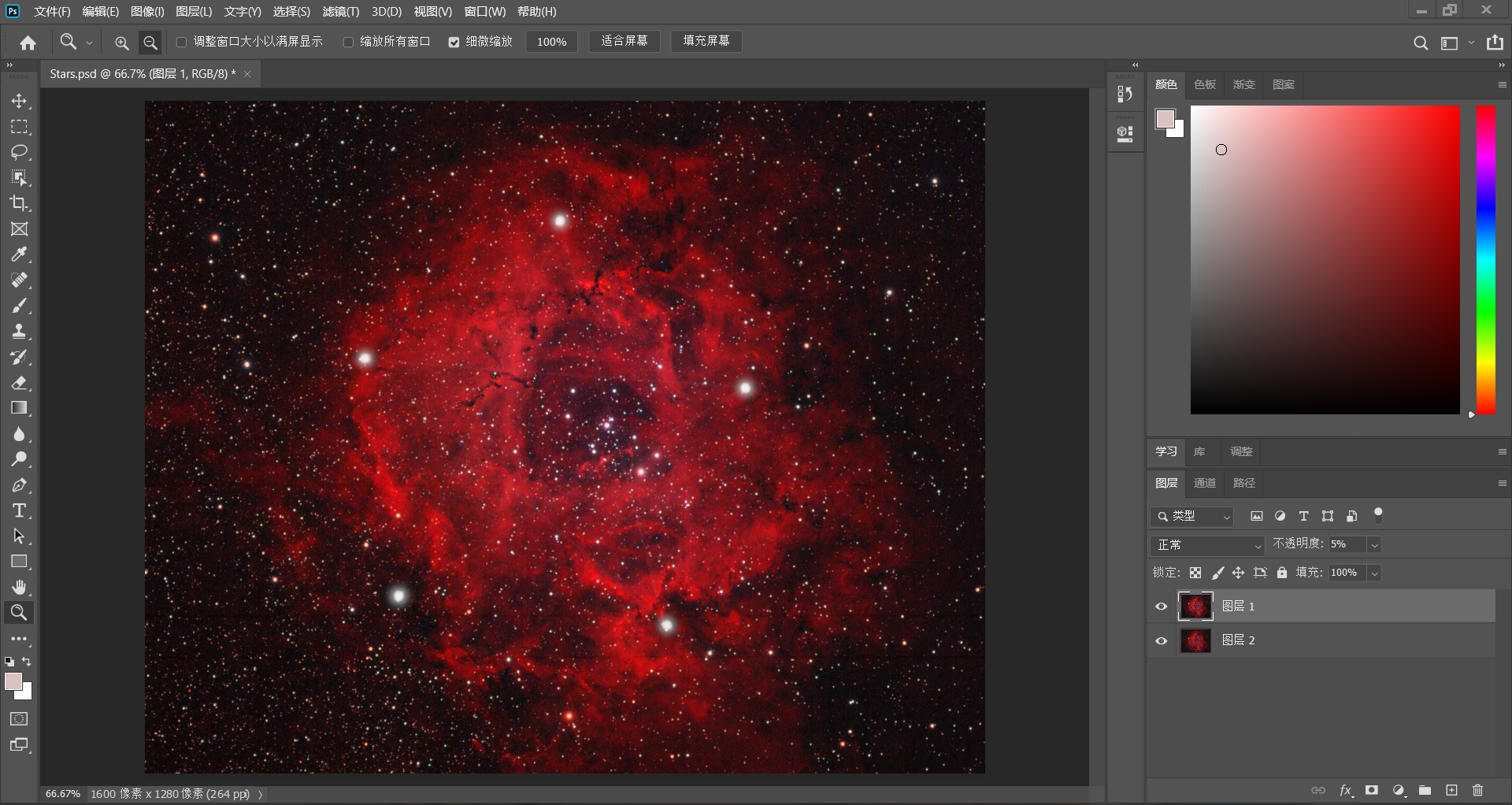
将第一个图层的不透明度拉高,可以看到有一个五角星
结合txt文件中的内容猜测是告诉我们排列顺序
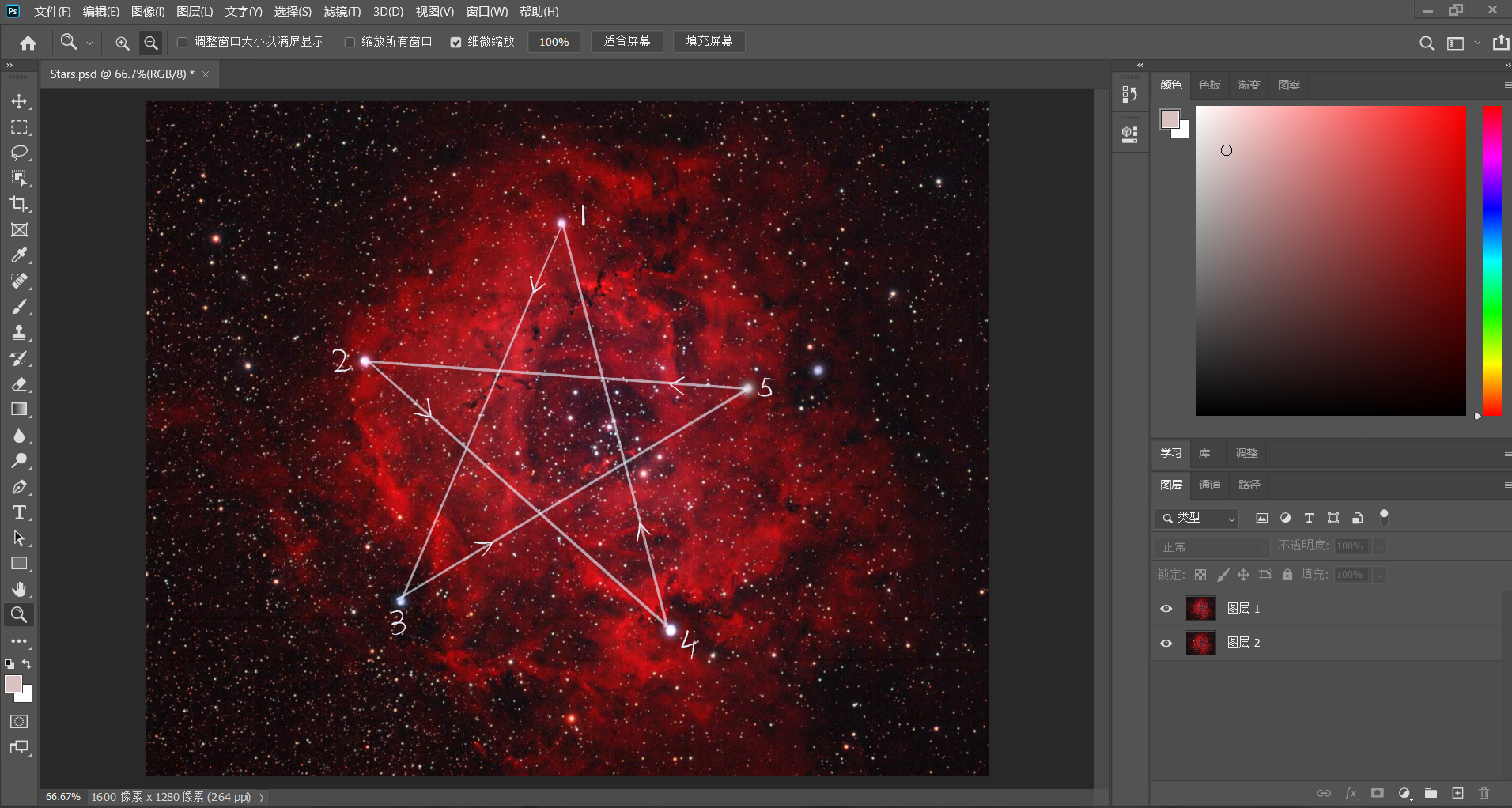
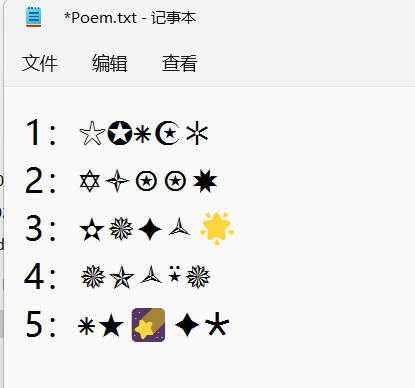
将记事本中的字符按照图片中的顺序排列后尝试当做excel的密码
打开excel后看到每一个字符对应的字母
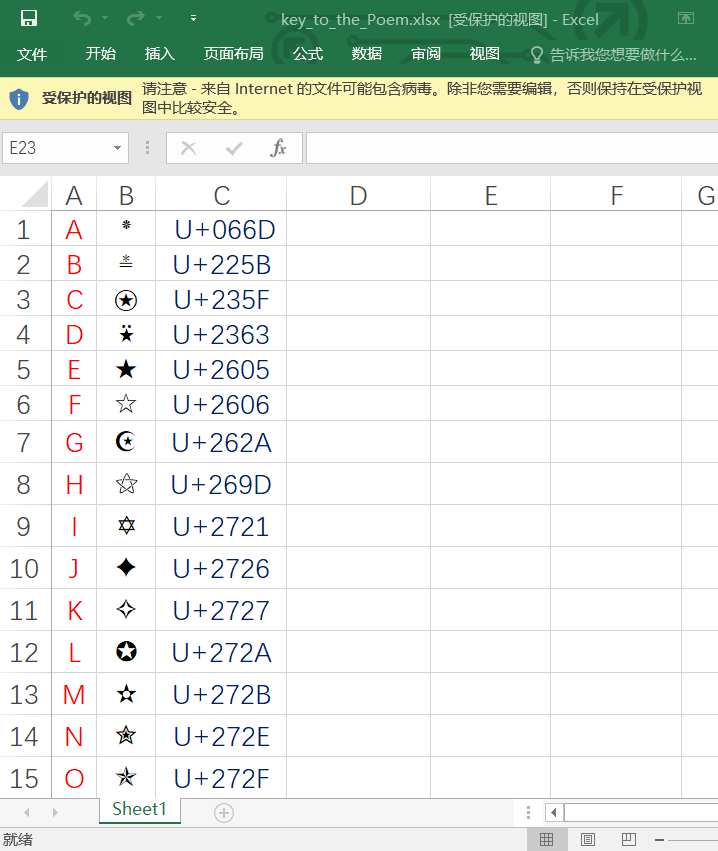
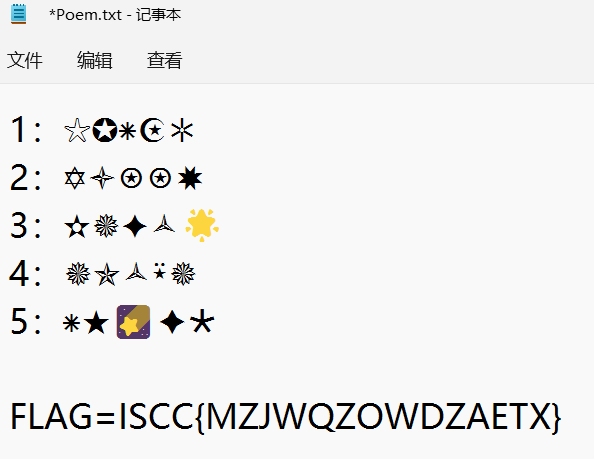
翻译一下,得到flag:
藏在星空中的诗2
下载附件 得到一个txt文件,乍一看毫无头绪

联系题目 , 藏在星空中的诗2 ,根据藏在星空中的诗那道题的excel附件
尝试翻译一下 txt文件中的内容
可以看出前三个字符是相同的,猜测为unicode 编码
每一个符号只取最后一位
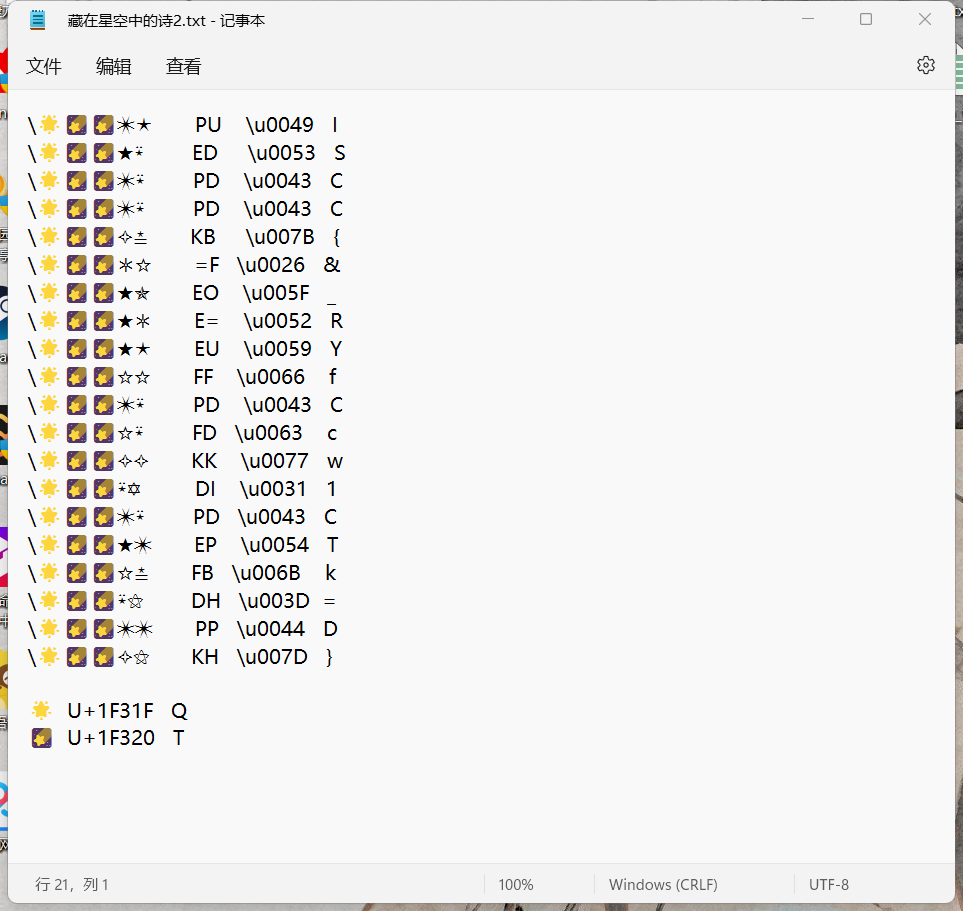
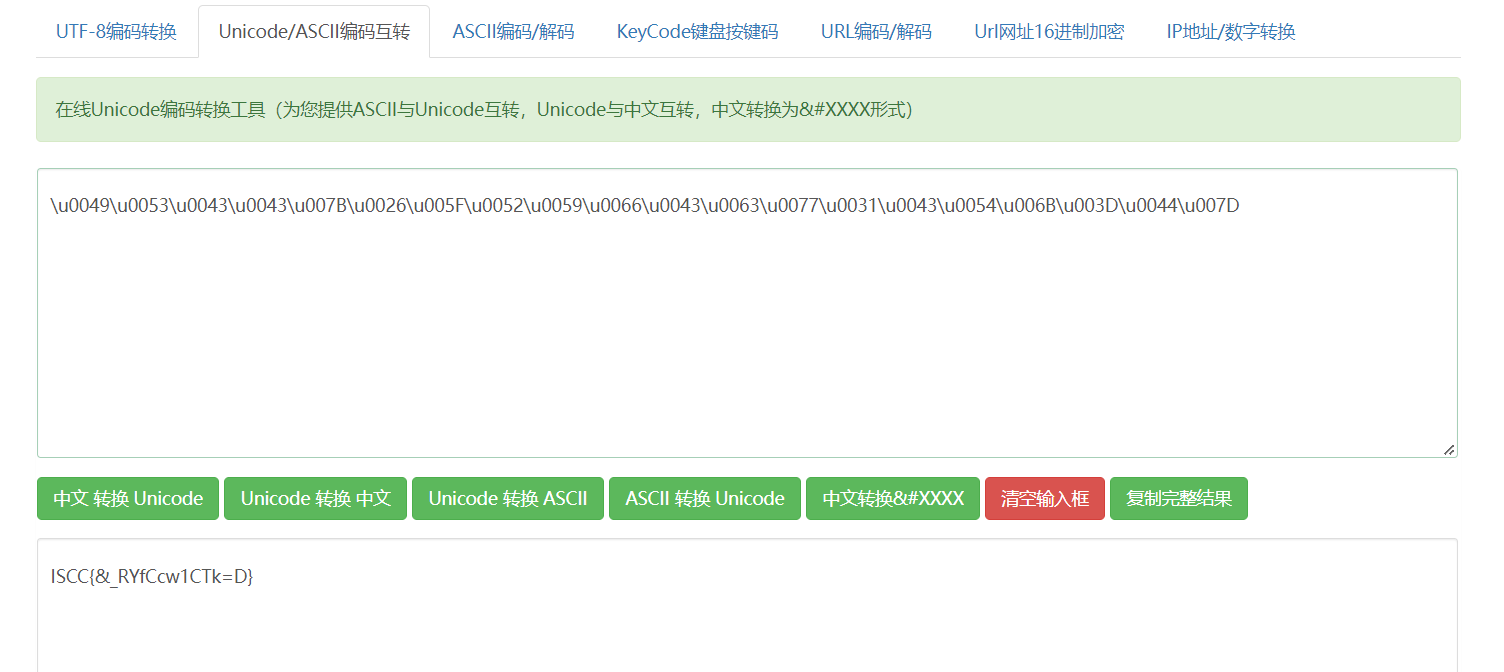
在线翻译一下即可得到flag
隐秘的信息
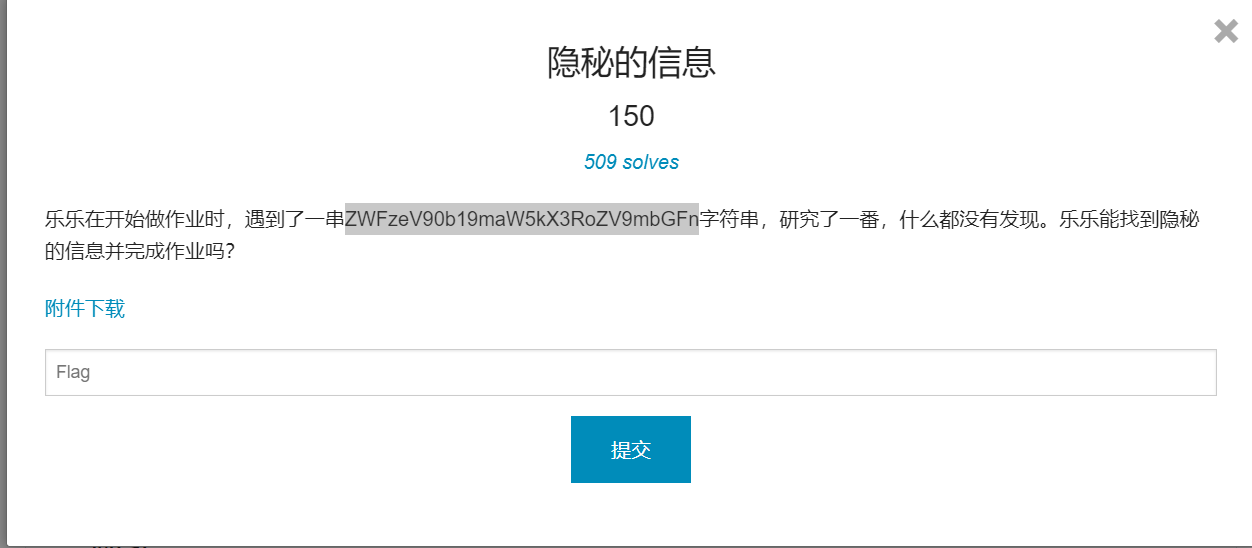
下载附件,发现是一个加密的图片,没有其他有用信息
看到题目中有一串怪异的字符串,拉去尝试解码,在base64下成功解出
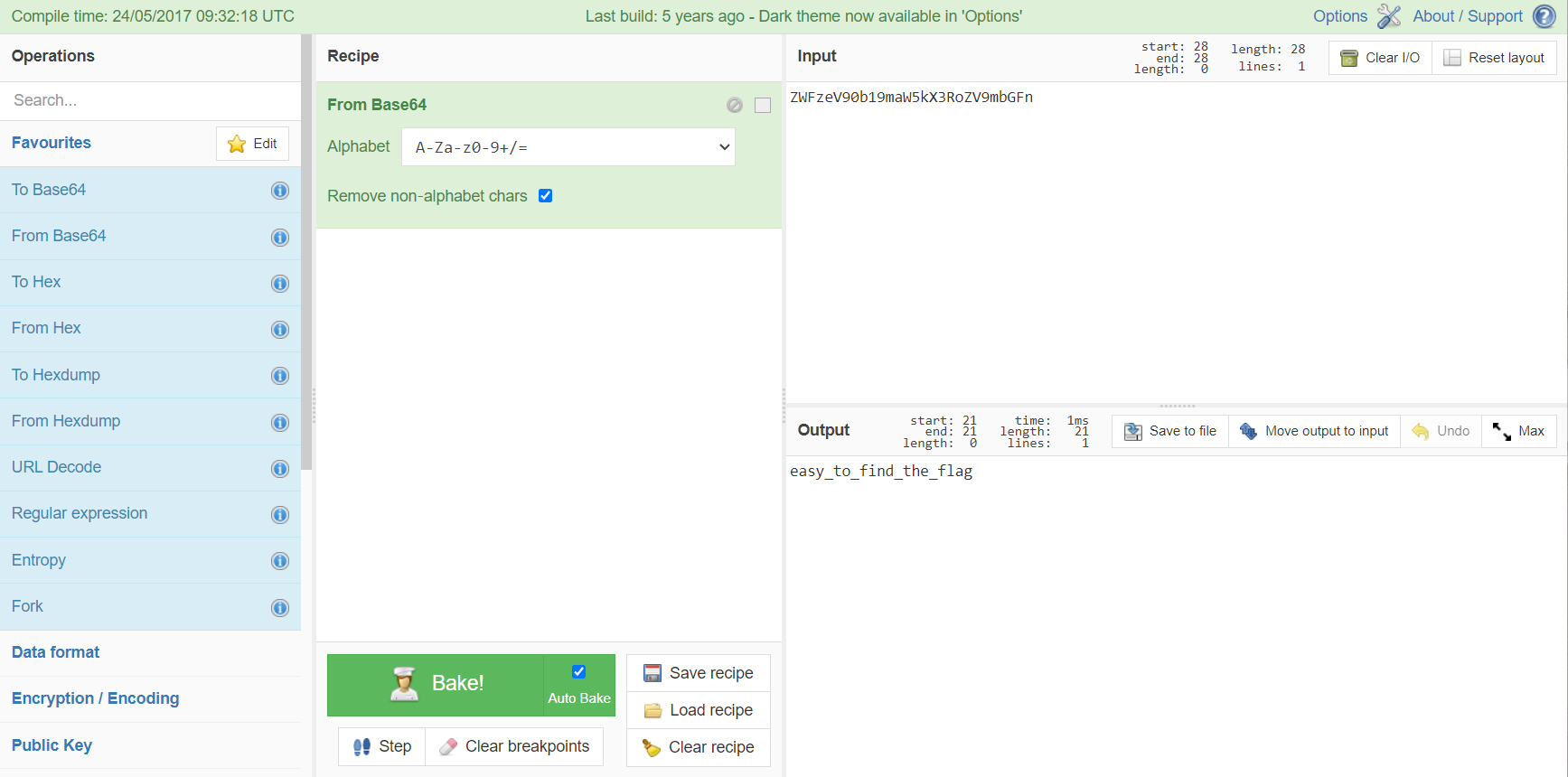
尝试当作密码,成功解开文件的加密,得到下面的图片

图片隐写,用stegsolve打开,查看LSB隐写
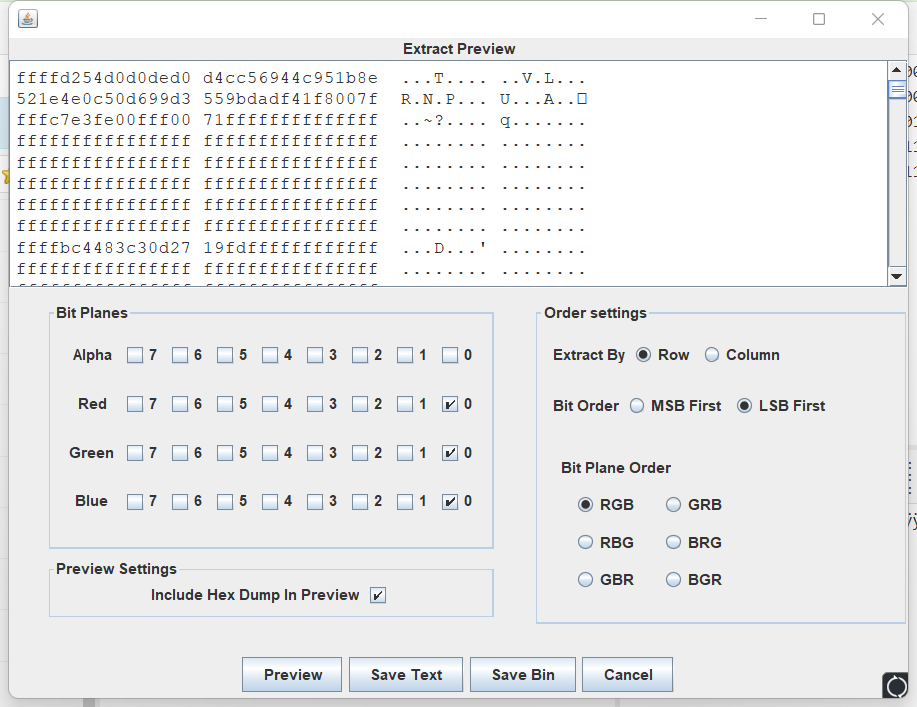
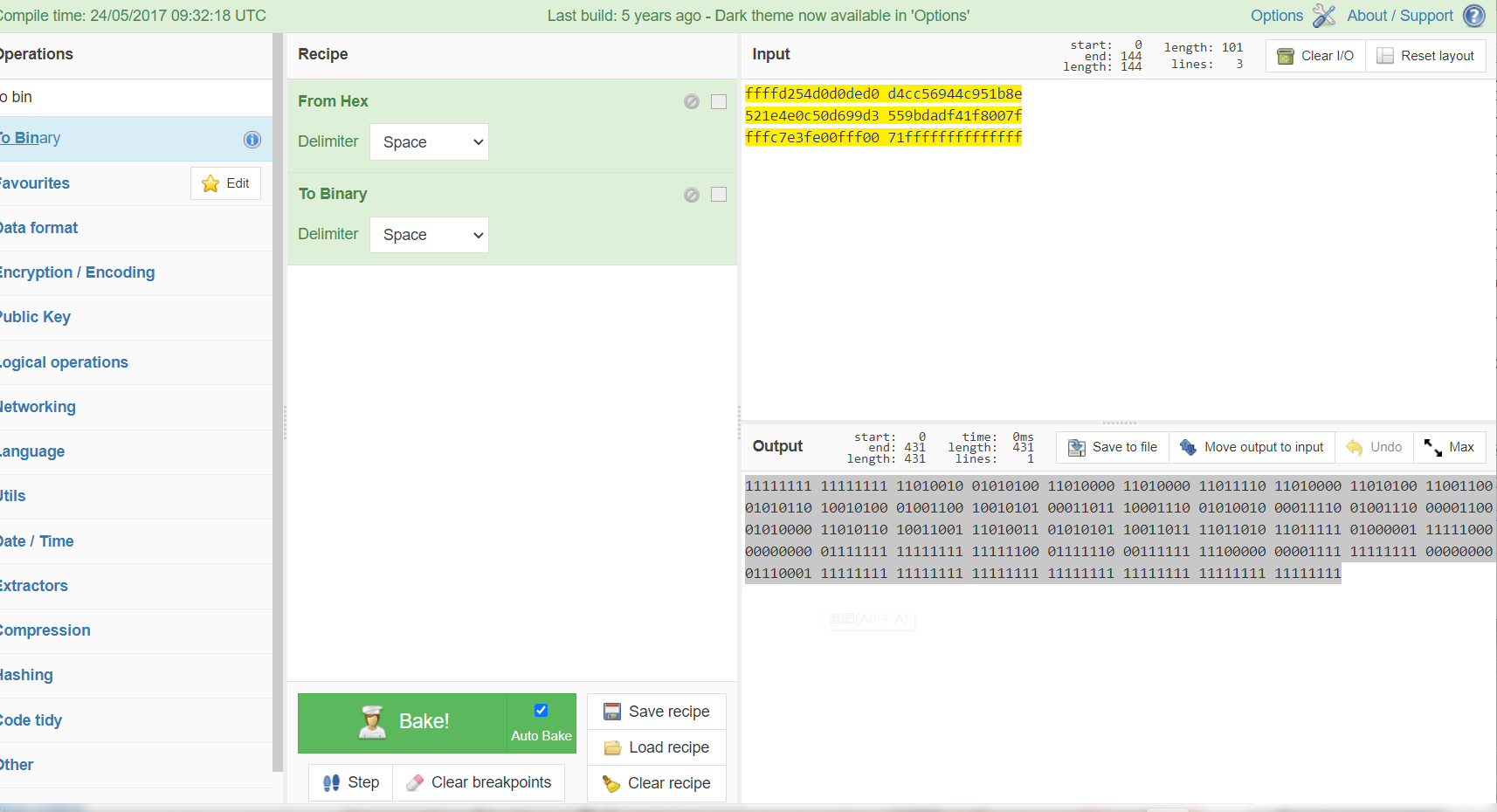
看到hex信息的前三行有所不同,拉去解密
Web
冬奥会
php代码审计
题目代码如下
1 |
|
year的判断条件中要求数组不是数字数组但要和2022相等
应该是php的弱类型比较
get传参即可得到flag
1 | /?Information={"year":"2022a","items":[0,[0],0]} |


